Secure IP Access At Last With Virtual TCP Online
Many companies agree that the Internet is a decent, low-cost, dial-up solution for mobile and remote users. Rather than buying and managing dedicated modem pools and dial-up services for all these users, many companies would rather use the Internet as a "free" connection—one that users can access from anywhere, saving in long-distance, equipment and personnel costs.
The major problem with this approach is security, or rather the lack of it. Opening your corporate networks, applications and data to anybody with an Internet connection is a scary proposition. InfoExpress hopes to allay such fears with its Virtual TCP Online encryption product, which provides a secure, encrypted link between a remote PC and a proxy host running on an internal corporate network. Users running Virtual TCP Online on their WinSock PCs can access their company's network and applications without fear of the connection being monitored or spoofed.
A Safe Haven
Virtual TCP Online achieves this by capturing and encrypting all TCP and User Datagram Protocol (UDP) packets generated on the PC, and then sending the encrypted data directly to the proxy host running on the internal corporate network. The proxy host decrypts the packets and sends them to their original destinations.
When data is returned, it is sent to the proxy host, which encrypts the packets and sends them on to the client. The client then decrypts the packets and hands them off to the relevant application.
This mechanism ensures that no data is sent from the PC to any host other than the proxy, and that the proxy is the only host that is communicating with the internal services on behalf of the remote users.
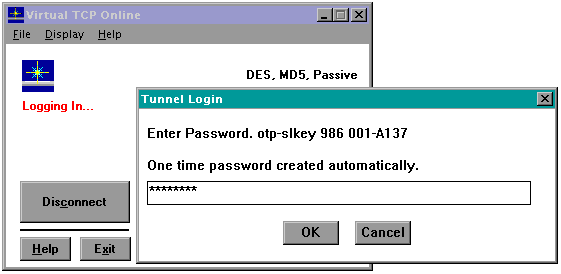
The encryption and authentication mechanisms are quite robust. When you first load the Virtual TCP Online client, you are asked to log in to an authentication host. The login host can be the proxy host or a Terminal Access Controller Access System (TACACS) server somewhere else on your network.
The login process uses a three-step challenge/response mechanism that implements private and public keys and one-time passwords. No reusable passwords are sent during the authentication process. Even the one-time user accounts and passwords are encrypted, preventing a casual sniffer from determining any of the login information.
The encryption process consists of two phases. First, the individual sessions use a specific key generated by the use of the Diffie-Hellman algorithms. (These prevent hackers from replaying any captured packets in a subsequent session.) Then either the 56-bit data encryption standard (DES) or the 112-bit triple DES is used for the actual encryption of the packets, depending on the configuration of the proxy host.
The client portion of the product is available for 16-bit Windows 3.x TCP/IP stacks, as well as 32-bit Windows95 stacks. The client login uses scripts that you can customize. If you require a client login to a proxy telnet server for authentication prior to accessing the Virtual TCP Online proxy host, you can create a script that does just that.
Virtual TCP Online's host portion is available for a variety of Unix systems, including HP-UX, AIX, Linux, SunOS and Solaris.